Many people think they are safe as long as they didn’t download anything from the internet. This is unfortunately NOT TRUE. Although most attacks start once the online user accidentally or unknowingly takes an action, some can secretly take place without the user’s knowledge or consent.
Some suspicious websites can be very dangerous and contain harmful content. While other regular ones might be also compromised and infected by third-party hackers. In either case, malicious code can be used to initiate cyber attacks on website visitors. In the first place, to steal sensitive information or exploit vulnerabilities in the victim’s machine.
Multiple threats may happen when you visit an unsecure website. Your personal information may be at risk or hackers can install malicious software on your device. Likewise, you might become a victim of a phishing attack, or others may track your behavior or consume your resources in their favor.
This article explains the most common dangers of visiting unsecure or malicious websites. For each threat, we describe how it happens, its potential risk, and what can be done to prevent it and protect ourselves. Finally, we discuss if the visitor can be hacked just by visiting an infected website.
1. Intercepting “Not Secure” Websites Communications
Risk Level: MEDIUM
Visiting a “Not Secure” website is one of the most known security concerns on the web. Primarily, because of the large number of affected websites.
Sometimes when trying to visit some websites, the browser automatically warns us that the website is “Not Secure”. It also shows a message saying that the connection to the website is not secure or not private.
When visiting a website with a “Not Secure” warning, all data and sensitive information being sent to the website can be stolen and modified.
This warning is primarily because the website is running on an unsafe HTTP protocol rather than a secure HTTPS protocol.
This happens because of any of the two reasons:
- Plain HTTP Protocol: the website is using plain HTTP, or it hasn’t automatically redirected the user to a secure HTTPS connection.
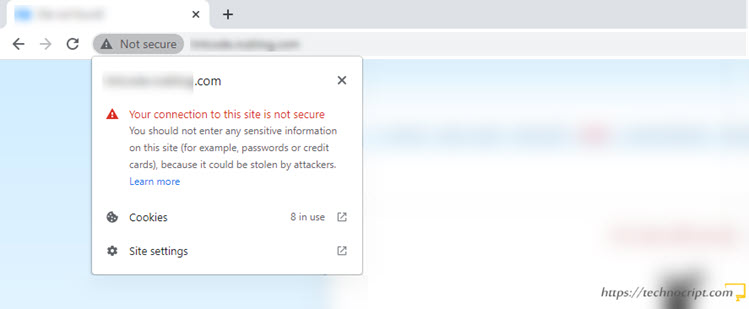
- Invalid HTTPS Protocol: The website already uses HTTPS, but its security certificate is expired or invalid.
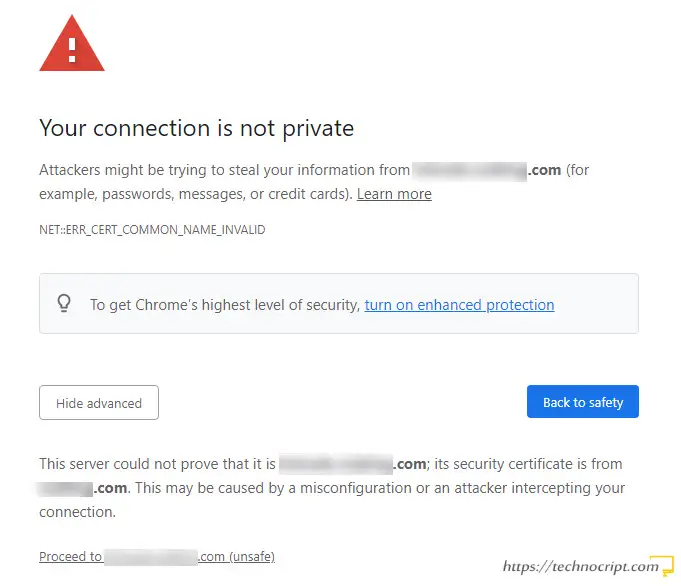
1.1. How “Not Secure” Websites Can Be Compromised
HTTP is the web protocol that sends our request to the web server, waits for it to respond, and then retrieves the visited website to be displayed on our browser.
By default this protocol is not encrypted, so all data are exchanged with the server in plain text. That said, anyone who manages to access the network can easily intercept the connection, modify its content, steal sensitive information, and redirect it to any other suspicious destination.
Therefore, the “Not Secure” warning doesn’t mean the website itself is not secure, but the communication between your browser and the website is insecure. Exactly similar to, for example, if your home and your friend’s home are both in safe areas but the way between them is not safe.
Attacks on insecure HTTP connections may happen in three ways:
- Stealing sensitive information: the data are in plain text so attackers can easily read the message and steal its content (ex. passwords and credit cards).
- Altering exchanged information: the data are unencrypted so hackers can alter the message without any means for others to detect this modification (ex. altering the bank account to receive money or injecting code in retrieved web pages).
- Redirecting to other websites: attackers can alter the requested URL and redirect it to a different destination (ex. to a suspicious website).
To know more about why HTTP protocol is not secure, we recommend reading our article: Is HTTP Secure? and Is It Really Safe to Visit HTTP Sites?
Is HTTP Secure? and Is It Really Safe to Visit HTTP Sites?
This article discusses the security concerns of HTTP protocol, why it is not totally secure, how safe it is, and what are the threats of visiting HTTP websites.
1.2. Potential Risks of Visiting “Not Secure” Websites
Visiting HTTP websites can be very risky because compromised data may include every single field being transmitted. From personal information like names and login credentials, to sensitive financial details like bank accounts and credit cards.
However, browsers often show this warning for any HTTP-only website. While there are many websites that are totally secure but they are still using HTTP. Generally, because they don’t exchange or collect sensitive information from their users. These websites are still classified as “Not Secure”.
Accordingly, the risk substantially decreases once the visitor avoids entering any kind of personal information when visiting HTTP websites.
Here are known threats that may take place when accessing a website using HTTP protocol:
- Man in the Middle Attack (MITM): the attackers place themselves between the user’s browser and the website server. Then they intercept the exchanged information to steal or alter it.
- Eavesdropping, Sniffing or Snooping: a passive MITM attack where hackers secretly listen to private communications. It basically aims at gathering information without altering and intercepting the connection.
- Parameter Tampering: a web-based cyber-attack that aims at changing the request parameters. Which might include configurations and other transactional details.
1.3. Protecting From Attacks on “Not Secure” Communications
The first defense mechanism to protect our transmitted data is to avoid visiting plain HTTP websites. When the browser tells you the website is “Not Secure”, just leave it and look for what you need on another secure one.
Furthermore, DON’T PROCEED to a “Not Secure” website unless there is no other option and you certainly know the website is safe and you trust it. Anyway, DON’T EVER ENTER SENSITIVE INFORMATION when visiting an HTTP website, because even if you trust it, you can’t trust the network.
On the other hand, HTTPS is the secure version of HTTP, it encrypts all exchanged information. Thus if the connection was intercepted, it can’t be modified and no sensitive data is leaked. Nonetheless, users can do nothing to secure a website as this is the responsibility of the website owner.
2. Installing “Drive-By Download” Malware
Risk Level: HIGH
Drive-by Download refers to the unintentional download of malicious code or harmful computer software from the internet to the user’s device.
It has two types based on whether the user granted permission to download the malware or not: authorized and unauthorized.
Both types of drive-by download attacks can happen when visiting an unsecure website. Often, by following an infected link, clicking on (or closing) a deceptive popup, or downloading a malicious program.
2.1. How Drive-By Download Attacks Happen
Authorized Drive-by Download: It happens when the user intentionally downloads software without knowing it’s infected. It is the most common type of this threat, as the visitor gives explicit permission to download and install the malware. Most often when downloading software from an untrustworthy website, or clicking on an unsafe link or popup that pretends, for example, to provide a fix for a problem in the victim’s machine.
Unauthorized Drive-by: it happens when the user has totally no idea the infected software has been downloaded. This type relies on vulnerabilities in the browser or its plugins. Which often can be found in outdated browser versions or poorly written extensions. That said, when visiting an infected website, the hidden scripts check for these gaps and exploit them to download and execute malware files from the internet.
In all cases, the victim ends up with drive-by malware downloaded and installed on his/her PC. Such programs expose users to different types of threats, including controlling the victim’s device, stealing information to send them back to the attacker, or interrupting the operating system and device accessibility or usability.
Can drive-by download attacks happen on legitimate websites?
Technically YES. Malicious software can be hosted on either an insecure or a “compromised” legitimate website. It can be also delivered by websites that deliver content from other platforms, such as advertisements.
Here is an example of a drive-by download attack taking place through a legitimate website:
- A hacker finds a legitimate website that doesn’t apply security filters to data submitted to a specific form.
- Cross-Site Scripting (XSS) step: the attacker successfully submits a malicious script to this website.
- When someone visits a specific page on the website where the script is being executed, a pop-up will appear.
- The user clicks on the pop-up or closes it, either way, he/she will be redirected to a new suspicious site.
- Drive-by Download step: this suspicious website, which won’t have been visited without the compromised legitimate site, leverages a vulnerability in the user’s browser. So it downloads and installs a virus or malware to the user’s computer.
2.2. Potential Risk of Drive-By Download Attacks
What makes this threat very dangerous is the ability for downloads to take place without being initiated by users. This gets more serious when the user doesn’t even know that something is going on behind the scene.
Moreover, attackers can use software called Exploit Kits that they can purchase or rent from underground criminal markets. Exploit kits run automatically as soon as a user visits the webpage, and then try to exploit security flaws in the web browser and its extensions. These kits are usually simple and do not require technical knowledge.
Furthermore, although modern browsers are getting much more secure and immune to all known security breaches, zero-day exploits can happen. Zero-day exploits are security flaws that haven’t yet been discovered, and thus were not fixed by the affected browser or software.
2.3. Protection From Drive-By Download Attacks
The first step toward preventing drive-by download attacks is to avoid accessing suspicious websites. You should also browse smartly, and be skeptical of any unexpected link or popup, particularly those that offer gifts, rewards, or provide error reports (DON’T EVEN CLICK ON “X” TO CLOSE THEM). Additionally, downloads should be strongly avoided from unknown, unofficial, or insecure sources.
On the other hand, the best protection against unauthorized drive-by download malware is to make sure you keep all your software up to date. This includes your browser, its plugins or extensions, the operating system, and any other software that has internet access.
Finally, maintaining a proper ad blocker and updated antivirus helps prevent suspicious malware from being downloaded and running on your machine.
3. Conducting Phishing Attacks
Risk Level: HIGH
Phishing is a cyber-security attack that includes sending fake messages that pretend to be from trusted sources.
The aim of phishing attacks is to trick users into unknowingly unveiling sensitive information. They may also deceive users to deploy malicious software on their machines.
Visiting unsecure websites puts visitors at phishing risks, basically by showing misleading messages and popups on the infected web pages.
Phishing is a social engineering attack because it relies on manipulating victims to convince them to do suspicious actions.
3.1. How Phishing Attacks Happen
Phishing attacks usually take place through an email spread with an infected link. They can happen on a suspicious website as well.
Here is an example:
When a user visits an insecure website, it shows some fake messages that try to push the user to click on a malicious link. The displayed messages usually appear in popups to segregate themselves from the visited website.
These messages usually contain links to suspicious websites. So if the victim was tricked by the message and clicked on the link, he/she will be redirected to a phishing website.
Most of the time, phishing websites pretend to be legitimate and delivered by reputable companies. Accordingly, they ask the victim to enter sensitive information to download software.
Since they seem identical to the original authentic websites, some victims tend to trust the website and take action based on what the website asks them to do.
3.2. Potential Risk of Phishing Attacks
Phishing is one of the most dangerous types of cyber security attacks. Because it passes through many security measures just because it convinces the users themselves to “unknowingly” initiate the attack.
When someone becomes a victim of a phishing attack, the consequences can be huge and severe. In most cases, the victims end up with their information has been stolen or malware has been downloaded to their computers.
3.3. Protection From Phishing Attacks
Being careful when navigating the web is the first step against phishing attacks. Insecure and shady websites should be strongly avoided, and any message or link that appears on them must be seen skeptically.
Furthermore, to protect online accounts from being stolen, enabling two-factor authentication is always a good security practice.
Finally, keeping an updated antivirus and antimalware can protect our computers from being compromised by suspicious software installed by phishing attacks.
4. Invisibly Mining Cryptocurrencies
Risk Level: LOW
Crypto mining is the process that cryptocurrencies like Bitcoin use to verify transactions and create new coins. Crypto mining usually requires very high computing power and a long time. To facilitate it and reduce its cost, this process can be spread among thousands of connected computers.
When visiting an unsecure website, cybercriminals can use visitors’ browsers to mine cryptocurrencies while landing on specific webpages.
4.1. How Invisible Crypto Web Mining Happens
Usually, this breach requires the miners to distribute malicious software. So that it can be secretly installed on the victim’s PC to make it part of the mining process.
However, It has been also found that the mining can be performed directly within the browser when visiting specific web pages.

This basically works by running a lightweight JavaScript (JS) file in the browser. This file contains the code needed to do the mining process and is simply downloaded and executed inside the visitor’s browser as part of the website files.
Additionally, the invisible mining can happen by a JS file of a minimized pop-up that hides under the main browser window. So that it continues to mine coins after other windows are closed. Hidden mining can also take place through ads delivered on the website.
That being said, this threat seems to be quite easy. It just requires the user to visit an infected site with the browser’s JavaScript enabled (which is by default in many browsers).
4.2. Potential Risk of Crypto Web Mining
Although this process uses additional resources without the visitor’s knowledge or explicit permission, the risk factor of web mining is low as well. Because of the following:
- This process just consumes additional resources from the victim’s machine while browsing the website.
- It stops as soon as the user closes or exits the browser/website.
- When stopped, It doesn’t leave negative or potentially harmful effects on the user’s machine.
4.3. Detecting and Preventing Crypto Web Mining
There are some methods to find and stop websites from mining cryptocurrencies when visiting them. Besides, one protection method is to disable JavaScript in the browser. Although this aggressive method would prevent any JS script to run, it will break many other benign websites that require JavaScript to function.
Other methods would be to use ad blockers or coin mining blockers such as NoMiner and minerBlock, or by monitoring and controlling the CPU usage.
5. Tracking User Behaviour (Tracking Pixels)
Risk Level: LOW
Web tracking is the process of monitoring, collecting, and analyzing internet users’ behavior anonymously when visiting a website. Usually for statistical, marketing, or commercial purposes.
Unsecure websites use a tracking technique called tracking pixels to spy on website visitors and track their behavior on the targeted website.
Most website monitoring platforms like Google Analytics do use similar techniques, this is usually disclosed in the hosting website’s privacy policy. Nonetheless, some shady platforms implement the tracking pixel technique without the knowledge and consent of visitors.
Tracking pixels are also used in emails to measure how many recipients have opened and read the newsletter.
5.1. How Tracking Pixels Work
Tracking Pixels is a simple HTML media element invisible to website visitors. It’s usually an image tag that has zero or 1×1 pixels dimension, or just has a white background.
The following is an example of how a tracking pixel might be. The src attribute refers to the URL from where the browser should download the image. In this case, it’s a location on the tracking server where the monitoring takes place.
<img width="0" height="0" src="https://TRACKING_SERVER/img.jpg">
Some websites implement the tracking pixel technique and don’t tell their visitors that they are being tracked. While some others are being infected with a tracking pixel by a third-party attacker.
When someone visits a page where a tracking pixel is injected, the image element is rendered as part of the visited page. Since the element is hidden or very tiny, it can hardly be noticed by visitors.
To load the element, the browser sends another request to the src link to fetch and “invisibly” display the image. This link is located on the tracking server. When this server receives the browser request, it responds to it and sends back the image element. Up until now, everything seems to be normal!
Since the browser sends a request to the external tracking server, it also sends additional information about the user’s browser, IP address, and details about the page being visited. Often, in the request header or as additional parameters to the image URL. These data are then recorded and analyzed by the tracking server without the user’s explicit agreement. Such information can be also sold to third parties to make a profit.
Here is how data can be appended to the image URL:
<img width="0" height="0" src="https://TRACKING_SERVER/img.jpg?id=123&page=sample_page&cat=cat1">
5.2. Potential Risk of Tracking Pixels
In most cases, the tracking pixel technique doesn’t seem to be very risky, specifically because it’s already being used by common advertising and traffic analysis platforms.
However, the problem here is that any type of information can be extracted and sent to the tracking servers. Which might include personal and sensitive information, in the worst case if the pixel was injected by hackers.
However, according to GDPR and privacy protection laws, users must be informed when their data are being collected. They should be also able to stop the tracking. This is not the case on an unsecure website infected with a tracking pixel.
5.3. Preventing Tracking Pixels
As the tracking pixel image element is considered part of the website itself, it’s pretty hard to detect and prevent them on web browsers. All websites do download multiple resources from external sources, such as fonts and CSS files, and the tracking image is nothing but another external resource.
For this reason, the most effective way to protect ourselves is to avoid visiting any suspicious or shady website. As well as to keep our sensitive information far from such kinds of untrustworthy websites.
Anyway, there are some generic web tracking blockers that might help prevent websites from tracking and monitoring our online behavior.
Can You Get Hacked Just By Visiting a Website?
When you open a website, your browser sends a request to the webserver to retrieve the visited webpage. This gives the server the right to download the webpage files on your computer. If the website was unsecure or infected, received files may contain malicious code that runs automatically after the page is loaded.
That being said:
You can get hacked just by visiting a malicious website, in milliseconds! Sometimes you don’t even need to click anywhere on the site, follow a seemingly safe link, give explicit permissions, or download anything from the website.
This type of attack is called drive-by download and usually happens on outdated browsers.
As explained earlier in this article, despite browsing the internet being totally controlled by the web browser, sometimes hackers exploit security flaws in your browser, its extensions, or the operating system. Which allows them to pass and download malware on your machine.
No one can claim that browsers are 100% secure. Many browser vulnerabilities (usually called zero-day exploits) were previously detected and fixed, for example on Chrome and Firefox.
Although such breaches mostly happen on shady websites, some regular ones can be infected as well by hackers. Furthermore, if the website is running on a plain HTTP protocol, malicious code can be injected with the website files by a third-party attacker who has access to the network.
Moreover, most advertisements on websites are usually served from external servers other than the website being visited. This makes ads possible means to carry infected codes to website visitors.
How can I get hacked by just visiting a website?
Here is an example of a possible scenario:
- Hackers manage to inject malicious code (ex. Exploit Kit) into a suspicious or compromised website.
- You visit the infected website or land on a specific page where the code is injected.
- The website files such as HTML, CSS, and JavaScript are downloaded to your browser to display the page, the code is downloaded as well (mostly as a JavaScript file).
- The malicious code runs automatically after the page is loaded, it starts looking for vulnerabilities in your browser or its extensions.
- If it found any vulnerability, the code exploits it to download and install malware on your computer.
How to avoid being hacked when visiting an unsecure website?
Fortunately, you don’t need to panic, although these types of attacks can be dangerous, they are rare and pretty hard to implement.
The first defensive mechanism to protect ourselves from being hacked is to detect and avoid visiting any suspicious link or website. Thus, we highly recommend reading through our comprehensive guide to know if a link is safe or not.

10 Indicators To Check If a Link Is SAFE? [With Examples]
We developed a comprehensive guide of all tips, tricks, and best practices to assess the safety of web links. Primarily, without clicking on the link to avoid any potential danger.
Moreover, all browsers are getting more secure day after day, putting urgent and extensive efforts into fixing security flaws before being exploited by hackers.
Here are some recommendations to minimize the possibility of being hacked when visiting websites:
- DO NOT USE OUTDATED BROWSERS: keep your browser updated (it is automatic for most browsers).
- Keep the browser extensions updated, and avoid installing plugins from untrusted sources.
- Browse smartly, don’t visit suspicious or shady websites, and don’t click on unsafe links.
- Avoid visiting “Not Secure” websites that run on plain HTTP protocol.
- Keep your operating system updated, and make sure you are using an up-to-date antivirus or antimalware (such as Malwarebytes).
- It is also a good idea to occasionally clean your browsing history, cookies, and cache.
Conclusion
Cybersecurity is the process of protecting networks, computer systems, and online users from being attacked. Websites are pretty common means to initiate cyber attacks that aim at stealing users’ data, tracking their behavior, and leveraging vulnerabilities in their machines. In many cases, the consequences of cyber-attacks can be extremely harmful and disruptive.
Being skeptical when browsing the internet and maintaining up-to-date browsers, operating systems, and antivirus are the first steps toward protecting ourselves and our privacy when visiting websites.