The digital signature is an authentication mechanism that enables content creators to attach a code to the content. So that this code acts as a signature of the content.
Due to the levels of security and reliability they provide, digital signatures are used as the preferred technology for signing online documents in many industries.
1. Overview
The digital signature is an e-signature being used to verify both the authenticity and integrity of digital materials. Such as emails, messages, documents, software, etc.
The digital signature cryptographically binds an electronic identity to a digital document using mathematical techniques. It aims at providing the highest level of assurance of the signer’s identity.
The ultimate goal of digital signatures is to ensure three main aspects:
- Authentication: the content was created by a known sender. Meaning that the person who created the content is the one who is represented in the signature.
- Integrity: the content was not changed or altered during transmission. Meaning that it is exactly how it was when signed by the signer.
- Non-repudiation: the entity who signed the content can’t deny, later, the ownership or validity of the signed content.
2. Digital Signature vs Handwritten Signature
Theoretically, digital signatures are equivalent to traditional handwritten signatures. Yet, they are modern alternatives to signing documents with paper and pen.

One of the main differences between them is the security and reliability levels provided by the digital form.
However, due to the encryption methodology behind digital signatures, they can’t be copied to other documents. On the other side, handwritten signatures could be easily replicated between documents. Either by digitally copying the signature image or by manually imitating it on other documents.
Additionally, traditional signatures usually exist only on the first/last page of the document. Making it fairly easy for other pages to be replaced after the signature is applied. Nevertheless, digital signatures are applied to the entire document. Being able to indicate the tampering or modification of any part of the document content.
3. Digital Signature vs Electronic Signature
Electronic signatures (or e-signatures) and digital signatures are often used interchangeably, but each one refers to a distinct and relatively different term.
Broadly speaking, e-signatures are the wide umbrella that covers the digital form of handwritten signatures. More specifically, an electronic signature is a legal concept that aims at capturing a person’s intent to be legally bound to an agreement or contract. Thus, the broader term of e-signatures often includes digital signatures.
On the other hand, a digital signature is a specific technique used to implement electronic signatures. It refers to encryption/decryption technology based on public-key cryptography. Thus, a digital signature itself is not an e-signature, it needs to be validated by an e-signing application to secure the e-signed documents.
4. The Idea of Digital Signatures
The main prenciple behind digital signatures is the usage of a pair of keys called: Public Key and Private Key.
4.1. Public Key Infrastructure
Digital signatures employ a set of standards called Public Key Infrastructure (PKI). This means each digital signature transaction combines two keys (two pieces of code): a public key and a private key.
As its name indicates, the private key must remain private and confidential. It should not be shared with others and is only used to sign the document.
On the other hand, the public key is not confidential and can be shared with all those who need to validate the signature.
4.2. How Do Digital Signatures Work?
Using the key pairs, digital signatures prove that the digital content was not modified since it was signed.
To do so, the sender generates a unique hash of the message or document. This hash is distinctive and tightly related to the content. Changing any part of the content will definitely change the hash. Then, the sender encrypts the generated hash using the sender’s private key.

Afterward, the signed content is sent to the recipient, along with the encrypted hash.
Once received, the recipient re-generates the content hash and decrypts the sender’s hash using the sender’s public key. Then, original and re-generated hash values are compared. If they match, the content was not modified and the sender is authenticated.
5. Digital Signature Process
As mentioned before, the digital signature process depends on hashing and encryption mechanisms. Where a pair of public and private keys are used.
To clearly explain this mechanism, we describe the individual steps of the entire process.
Let’s consider this scenario: a sender (S) is sending a document (DOC) to a recipient (R):
5.1. Sender Side:
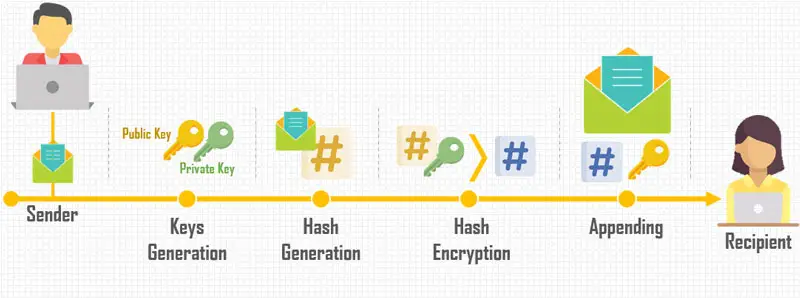
- Keys Generation: a key generation algorithm randomly generates two unique keys for the sender. A public key (PBK) and a private key (PVK).
- Sender Hash Generation: a unique hash (HSH) is generated for the document (DOC). Any modification to the content will modify the hash.
- Hash Encryption: the generated hash (HSH) is encrypted using the sender’s private key (PVK). The resulting hash is (EHSH).
- Appending: the encrypted hash (EHSH) and sender’s public key (PBK) are appended to the document (DOC).
- Sending: the message is sent to the recipient (R), which contains the sender’s document (DOC), sender’s encrypted hash (EHSH), and sender’s public key (PBK).
At this stage, the document hash which was generated and then encrypted using the sender’s private key is called the document’s digital signature.
The following figure describes the digital signature steps on the sender side.
5.2. Recipient Side:
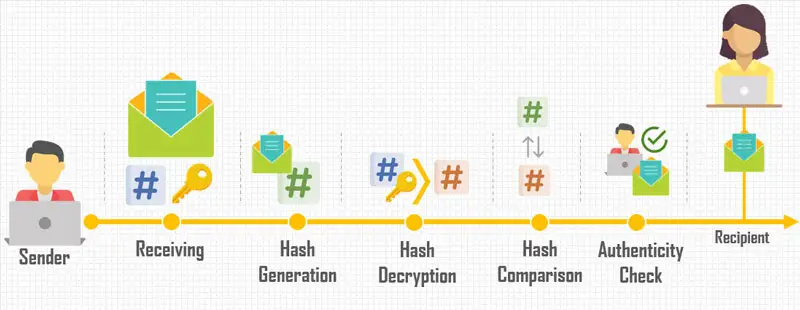
- Receiving: the recipient (R) receives the message with its three elements, assuming no modifications were made to any of them.
- Recipient Hash Generation: upon receiving the document (DOC), the recipient re-generates the document’s hash. The resulting hash is (HSH2).
- Hash Decryption: using the sender’s public key (PBK), the recipient decrypts the received encrypted hash (EHSH). The resulting hash is (HSH).
- Hash Comparison: the recipient’s re-generated hash (HSH2) and the sender’s decrypted hash (HSH) are compared to each other.
- Authenticity Check: if the compared hashes match, the document (DOC) was not altered and it is accepted. Otherwise, modifications have been made to at least one of the three elements, and the entire message is rejected.
The following figure describes the digital signature steps on the recipient side.
6. Is Digital Signature Legally Acceptable?
As mentioned before, the digital signature is an implementation of the legal concept of e-signatures. It produces a unique digital fingerprint for a person or entity and uses it to identify digital users and protect their information.
Nowadays, e-signatures are widely accepted as a legal method for digitally signing documents. They are currently the safest and most accepted methods for the legal representation of a digital identity.
Digital signatures are considered legal and hold the same position as traditional handwritten signatures in many regions. Nevertheless, we always recommend seeking independent professional advice to check if digital signatures are accepted, considering the region and context where they are being used.
7. Digital Certificate vs Digital Signature
Digital certificates and digital signatures are closely related concepts being used interchangeably. From a technical perspective, digital certificates and digital signatures refer to different things.
The digital signature uses a pair of keys to work. One of them is public and can be shared with any party which needs to validate the signature. Remember that digital signatures are also used to validate the identity of the message, not only if it has been altered on its way.
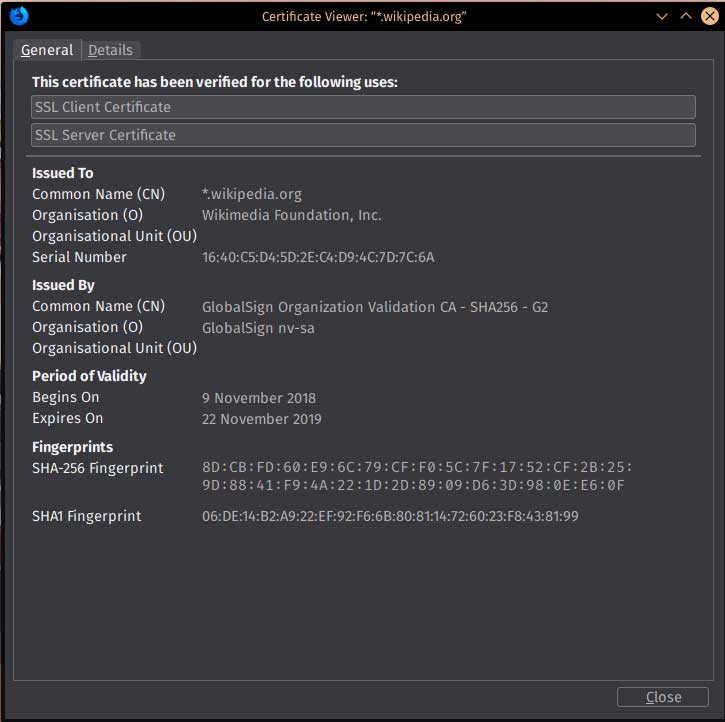
In this context, the digital certificate (also known as a public-key certificate or identity certificate) is a digital document being used to prove the ownership of the public key.
Hence, once the message is received and successfully validated, the recipient uses the digital certificate to verify the identity of the sender.
A digital certificate often contains:
- Public Key Info: details about the public key.
- Subject Name: details about the public key owner identity.
- Issuer Name: the digital signature of the entity that has issued the certificate, also called Certified Authority (see the next paragraph).
- Validity: details about issuance and expiration dates.
- Other related information.
8. Certificate Authority (CA)
For each digital signature transaction, a pair of public and private keys are used. Certificate Authority (CA) is a trusted organization recognized for issuing and maintaining these keys.
That being said, CA is a trusted third party that generates public and private keys and validates the entity identity using the digital certificate.
Once a certificate authority validates an identity, it provides a digital certificate that is digitally signed by this authority. This digital certificate can be used later to verify the person’s identity associated with the public key.



I have a question, if you encripted the first hash (HSH) with the private key of the sender (PVK), then how could you undo that process using the public key if they are not the same, and if the answer to that question is that you do not encrypt the original hash with the private key, you just append them or something like that, then how can be guarantied that no one will be able of tampering with the message on-route and change whatever they want if they have all that they need right there on the message body, like the public key and the original document itself, besides, that approach does not leave also the chance for an attacker to access the private key of the signer wich is, in my opinnion, even worst?
My intention is not to be criticize, I just want to understend how does this work cause I’m tring to nail an implementation.
Thank you ebm for sharing your inquiry.
The keys are NOT the same, otherwise, it doesn’t make sense to use two separate keys.
This kind of encryption is called Asymmetric Cryptography (or Public-key Cryptography), where a specific algorithm is used to generate a pair of keys based on a mathematical relationship. Any data encrypted using the private key can be decrypted only with the corresponding public key (and vice versa).
Keep in mind that the terms “public/private” keys are used based on the context. In message encryption where the goal is to hide the message content, the public key is used for encryption while the corresponding private key is used for decryption. In digital signatures where the aim is to ensure the identity, they are used the other way around. Anyway, you have two keys, one of them should keep secret and the other can be exchanged.
For more information, please check the following sources: